9 Configuring Oracle Database Vault Policies
You can use Oracle Database Vault policies to implement frequently used realm and command rule settings.
- What Are Database Vault Policies?
An Oracle Database Vault policy groups local realms and command rules into a named policy that you can enable or disable as necessary. - Default Oracle Database Vault Policies
Oracle Database Vault provides two default policies that you can use to better secure user accounts and system privileges. - Creating an Oracle Database Policy
To create an Oracle Database Vault policy, you create a container policy that specifies the realms and command rules that encompass the policy. - Modifying an Oracle Database Vault Policy
You can use Enterprise Manager Cloud Control to modify an Oracle Database Vault policy. - Deleting an Oracle Database Vault Policy
You can use Enterprise Manager Cloud Control to delete Oracle Database Vault policies. - Related Data Dictionary Views
Oracle Database Vault provides data dictionary views that are useful for analyzing Database Vault policies.
What Are Database Vault Policies?
An Oracle Database Vault policy groups local realms and command rules into a named policy that you can enable or disable as necessary.
- About Oracle Database Vault Policies
Oracle Database Vault policies can group realm and command rule definitions into one policy, which then can be collectively enabled or disabled. - Oracle Database Vault Policies in a Multitenant Environment
Oracle Database Vault policies are only local to the pluggable database (PDB) in which they were created.
Parent topic: Configuring Oracle Database Vault Policies
About Oracle Database Vault Policies
Oracle Database Vault policies can group realm and command rule definitions into one policy, which then can be collectively enabled or disabled.
Database Vault policies enable you to delegate limited realm administration privileges to database users without giving them the powerful privileges that the DVADM and DVOWNER roles provide. Oracle Database Vault provides default policies.
For example, suppose you have a set of Oracle Database Vault objects that are related to a particular application, such as a realm and several command rules. You can use a Database Vault policy to group these objects into one policy. You then can designate a policy administrator to manage adding users to a realm for this application and for enabling or disabling the policy. If there is only one primary application, then it can be used for manageability where a user can enable, disable, or simulate (use simulation mode) all related objects with one command rather than issuing a command for each included Database Vault object.
How the enablement of the individual realms and command rules works depends on how you set the policy state of the policy, as follows:
-
Full enabled mode (
DBMS_MACADM.G_ENABLED) sets the policy to take precedence over the individual enablement settings of the associated realms and command rules. For example, if the associated objects of a policy are individually disabled, then they will be enabled if the policy is enabled. (Conversely, you can setDBMS_MACADM.G_PARTIALto allow the embedded security objects to set their own enabled, disabled, or simulation mode.) -
Partial enabled mode (
DBMS_MACADM.G_PARTIAL) enables the associated realms and command rules to have different status settings (ENABLED,DISABLED, andSIMULATION). The other policy status choices force all associated controls to the same status dictated by the policy. Setting the policy status to partial allows each realm and command rule to change status as required. -
Simulation mode (
DBMS_MACACM.G.SIMULATION) enables the policy but writes violations to realms or command rules to a designated log table with information about the type of violation, such as a user name or the SQL statement that was used. Simulation forces every security object in the policy to be in simulation mode. -
Disabled mode (
DBMS_MACADM.G_DISABLED) disables the policy after you create it.
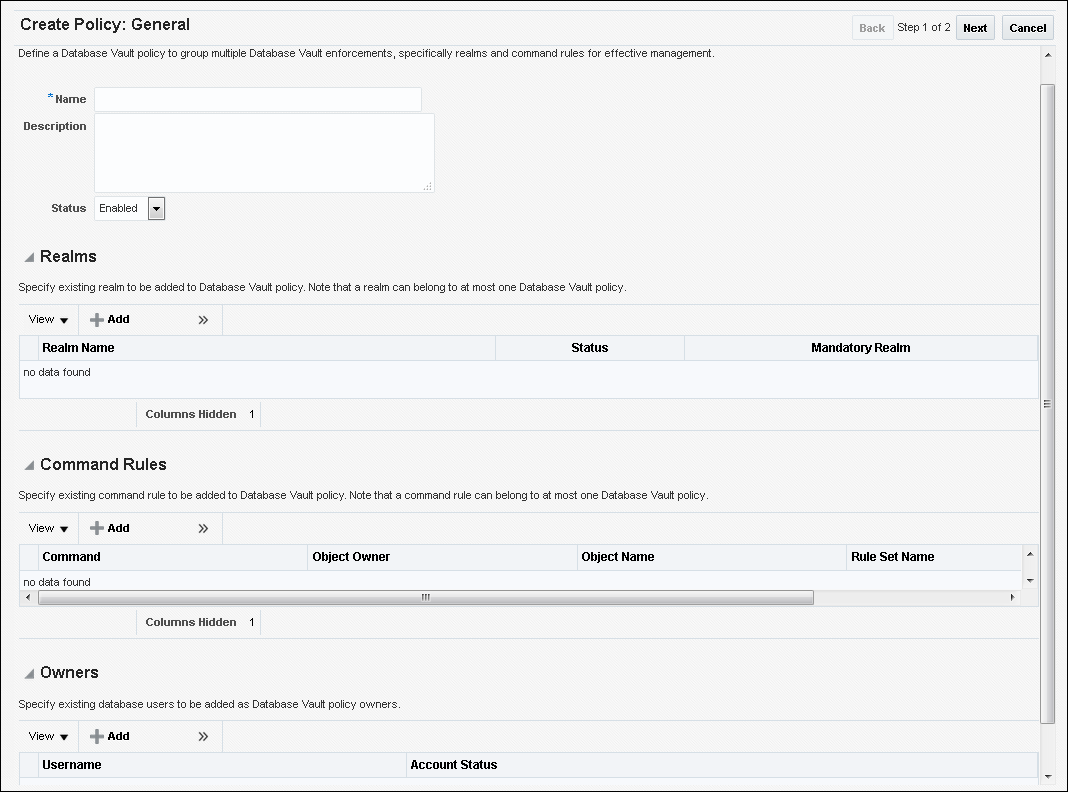
In general, to create a Database Vault policy, you perform the following steps:
-
Create the necessary realms and command rules to use in the policy.
-
Create the Database Vault policy.
You can use the
DBMS_MACADM.CREATE_POLICYprocedure to create the policy. -
Add one or more realms to the policy.
You can use the
DBMS_MACADM.ADD_REALM_TO_POLICYprocedure to add realms to the policy. -
Add one or more command rules to the policy.
You can use the
DBMS_MACADM.ADD_CMD_TO_POLICYprocedure to add command rules to the policy. -
Add one or more database users as owners of the policy.
You can use the
DBMS_MACADM.ADD_OWNER_TO_POLICYprocedure to add users to the policy. Afterward, grant this user theDV_POLICY_OWNERrole. This user will be able to perform a limited set of tasks: changing the policy state, adding or removing authorization from a realm, and having theSELECTprivilege for a set of theDVSYS.POLICY_OWNER* data dictionary views. By default, theDVOWNERuser owns the policy.
After the policy is created, it can be used right away.
This section explains how to configure policies by using the Oracle Database Vault Administrator pages in Oracle Enterprise Manager Cloud Control. To configure policies by using the PL/SQL interfaces and packages provided by Oracle Database Vault, you must use the DBMS_MACADM PL/SQL package.
Oracle Database Vault Policies in a Multitenant Environment
Oracle Database Vault policies are only local to the pluggable database (PDB) in which they were created.
That is, if you created the policy in a PDB, then only local realms and command rules can be added to it. You cannot create Database Vault policies that can have common realms or common command rules.
Parent topic: What Are Database Vault Policies?
Default Oracle Database Vault Policies
Oracle Database Vault provides two default policies that you can use to better secure user accounts and system privileges.
You can use the default policies in your own security configurations. If you do not need them, then you can remove them because they are not needed for internal use by Oracle Database Vault.
The default policies are as follows:
-
Oracle Account Management Controls enforces controls over user-related operations within Oracle Database Vault. It is used to prevent ad hoc user account creation, user deletions, and other user account-related operations by unauthorized privileged users. It includes the Database Vault Account Management realm and user account management command rules for SQL statements such as
CREATE USER. -
Oracle System Protection Controls enforces controls on important database schemas, privileges, and roles that are associated with the default Oracle Database environment. It includes the realms such as Oracle Default Schema Protection Realm and command rules for the system management SQL statement
ALTER SYSTEM.
Related Topics
Parent topic: Configuring Oracle Database Vault Policies
Creating an Oracle Database Policy
To create an Oracle Database Vault policy, you create a container policy that specifies the realms and command rules that encompass the policy.
Parent topic: Configuring Oracle Database Vault Policies
Modifying an Oracle Database Vault Policy
You can use Enterprise Manager Cloud Control to modify an Oracle Database Vault policy.
- Log in to Oracle Database Vault Administrator from Cloud Control as a user who has been granted the
DV_OWNERorDV_ADMINrole and theSELECT ANY DICTIONARYprivilege. Logging in to Oracle Database Vault from Oracle Enterprise Cloud Control explains how to log in. - In the Administration page, under Database Vault Components, click Policies.
- Select the row for the policy that you want to change.
- Click Edit.
- In the Edit Policy page, modify the settings as necessary.
- Click Next, and then click Finish.
Parent topic: Configuring Oracle Database Vault Policies
Deleting an Oracle Database Vault Policy
You can use Enterprise Manager Cloud Control to delete Oracle Database Vault policies.
- Log in to Oracle Database Vault Administrator from Cloud Control as a user who has been granted the
DV_OWNERorDV_ADMINrole and theSELECT ANY DICTIONARYprivilege. Logging in to Oracle Database Vault from Oracle Enterprise Cloud Control explains how to log in. - In the Administration page, under Database Vault Components, click Policies.
- Select the row for the policy that you want to delete, click Delete, and then click Yes in the confirmation dialog box.
Parent topic: Configuring Oracle Database Vault Policies
Related Data Dictionary Views
Oracle Database Vault provides data dictionary views that are useful for analyzing Database Vault policies.
Table 9-1 lists data dictionary views that provide information about existing Oracle Database Vault policies.
Table 9-1 Data Dictionary Views Used for Oracle Database Vault Policies
| Data Dictionary View | Description |
|---|---|
|
Lists the Database Vault policies, a description, and their state |
|
|
Provides detailed information about the policies, such as the associated realms and command rules |
|
|
Lists the owners of Database Vault policies |
|
|
Enables users who have been granted the |
|
|
Enbles users who have been granted the |
|
|
Enbles users who have been granted the |
|
|
Eenables users who have been granted the |
|
|
Eenables users who have been granted the |
|
|
Enables users who have been granted the |
|
|
Enables users who have been granted the |
|
|
Enables users who have been granted the |
|
|
Enables users who have been granted the |
Parent topic: Configuring Oracle Database Vault Policies